The Cryptography Conundrum
Moral, pure, political or subversive?How can cryptographers develop more effective means to resist unlawful mass surveillance?
http://alcuinbramerton.blogspot.com/2015/12/the-cryptography-conundrum.html
Alcuin Bramerton Twitter .. Alcuin Bramerton Medium
Alcuin Bramerton profile ..... Index of blog contents ..... Home .....#1ab
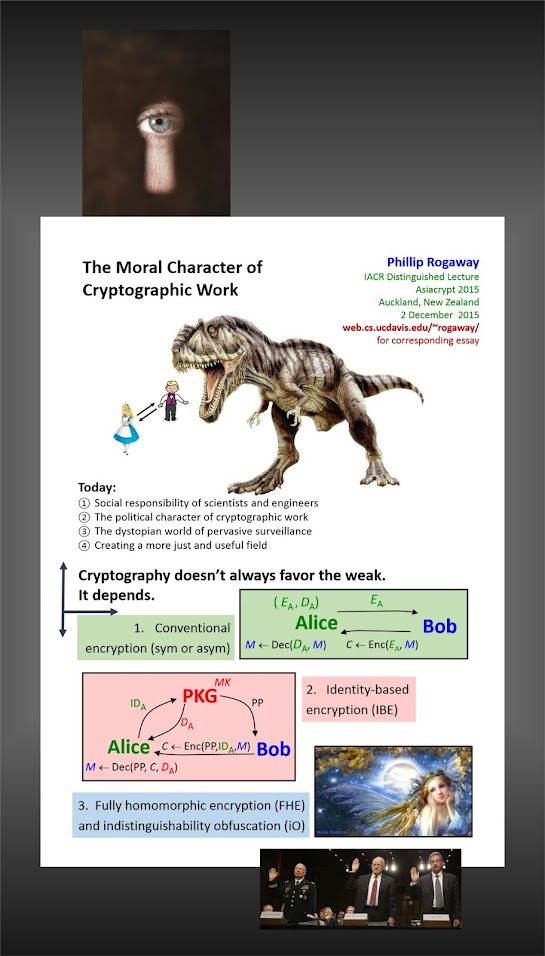
Picture: The Morals of Cryptographic Work. Phillip Rogaway. AsiaCrypt 2015.
......................................................................
We live immersed in a parasitically interconnected world of nearly unavoidable electronic communications.
Most of the data we generate in that world is unknown to us. Our data is stolen and exploited by invisible Others who know much more about us than we know about them.
We have an agenda for our electronic lives; so do the Others.
Since WikiLeaks, Chelsea Manning and Edward Snowden, we have learned that our electronic agenda and the electronic agenda of the invisible Others of BigData do not always coincide in perfect purity. There is good at work; but there is also evil. There are goodies and there are baddies.
This is one reason why, at the highest levels of state intelligence, Russia is said to be making and using manual typewriters again.
None of that sovereign state's most important planning, recording or analytical documentation is generated or stored electronically. Its paper-only documents are designed to exist beyond the reach of hackers or electronic surveillance.
Russia and others have moved in this direction because, in the world of computer networks, cryptography has failed.
The cryptographers are bought and paid for. As a species, they can no longer be trusted. As an intellectual culture, the cryptographic community has allowed itself to become fatally compromised by ulterior motives.
Cryptography is about code and about how to write it in covert functioning formats for computer networks.
Cryptography is supposed to employ methods of storing and transmitting data in particular forms so that only those for whom it is intended can read and process it. Peeping Toms, voyeurs and electronic tourists are supposed to be designed out. No access. Instead, unscrupulous cryptographers provide the lice with privileged back doors through which to creep in.
Privacy, cryptography and surveillance are overlapping domains.
In December 2015, at AsiaCrypt2015 in New Zealand, Phillip Rogaway of the Department of Computer Science at the University of California, Davis, US, delivered a lecture which raised urgent questions about the moral character of cryptographic work.
Cryptography, he argued, rearranges power; it congures who can do what, from what. This makes cryptography an inherently political tool, and it confers on the field an intrinsically moral dimension.
The Edward Snowden revelations, and others of a similar kind, motivate a reassessment of the political and moral positioning of cryptography. They lead professional cryptographers to ask if their inability to effectively address mass surveillance constitutes a failure of their specialist field.
Rogaway believes that it does. He calls for a community-wide effort by cryptographers to develop more effective means to resist mass surveillance.
He pleads for a reinvention of cryptographic culture to attend not only to puzzles and mathematics, but also to the societal implications of the coding work done.
The full text of Phillip Rogaway's lecture is here (12.12.15: pdf 48pp). And his lecture slides are here.
AsiaCrypt2015 took place from Sunday 29th November to Wednesday 2nd December 2015 in Auckland, New Zealand.
Picture: Peeping Tom. Keyhole. Key. The Moral Character of Cryptographic Work.

......................................................................
Thanks to: http://alcuinbramerton.blogspot.com






 Sat Mar 23, 2024 11:33 pm by globalturbo
Sat Mar 23, 2024 11:33 pm by globalturbo

